SECURITY SOLUTIONS
THE GLOSEC SECURITY DOCTRINE
DO ADVANCED SECURITY SYSTEMS ACTUALLY PROMISE SECURITY? NOT REALLY
THE FIRST GENERATION
Glosec specializes in HLS, defense and security solutions, and is committed to advanced technology and proven solutions. Sep 11th 2001 was a “turning point” in Homeland Security. It is than that the abbreviation HLSwas created, as governments all over the world began allocating budgets to homeland security. Glosec’s experience goes back decades, far before 9-11. When we started out 40 years ago, our 1st generation security solutions were all about “Monitoring Security”, using advanced CCTV for surveillance and observation.We call this “Reaction mode
THE SECOND GENERATION
Later, due to new emerging needs, we advanced to our 2nd generation of “Integrated Security” – machine with machine, sensor with software, communications, hardware, detectors, cameras, controllers, integrating varioussub-systems into one integrated solution.

TODAY
With the increase and sophistication of threats around the world, we see that even the most smart and advanced security system cannot really guarantee security since they all lack real attention to the human factor. Hardware and intelligent integration is not sufficient anymore. This is what made us re-think our security doctrine and evolve into the next generation.
THETHIRDGENERATION
Our 3rd generation security doctrine focuses on six main areas integrated into one holistic approach – In House Risk Analysis, Value Engineering, Human Resource, Protocols & Working Procedures, Training & Coursesand Preventive & Corrective Maintenance. Together they guarantee – as a holistic solution – the efficiency and effectiveness of our clients’ security.
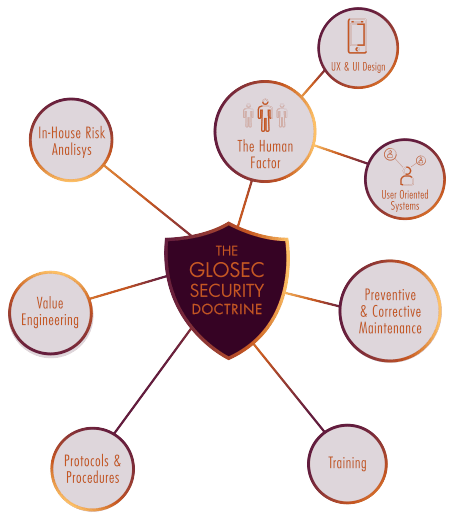
- THE HUMAN FACTOR
THE HUMAN FACTOR
- In house risk analysis
In house risk analysis
- Value engineering
Value engineering
- Protocols & Working Procedures
Protocols & Working Procedures
- Training & Courses
Training & Courses
- reventive & Corrective Maintenance
reventive & Corrective Maintenance
It’s a known fact that the weakest link in the complex chain of security, is almost always human. A significant part of the challenges lies in the gap between the human operator and the technological systems he or she is supposed to operate.
It’s much easier to make sure that a baggage scanner is working properly. Such a machine is checked, double checked and then triple checked, and has to adhere to severe standards. But, even if we’re satisfied with the machine, we have limited knowledge about the capabilities and reactions of the machine operator, a person standing in front of a monitor during the late hours of the “graveyard shift” at a large European airport. And this goes also for any other human security operator, anywhere around the world, even the most highly trained operative
OUR GOAL – USER ORIENTED SYSTEMS
From the moment we put humans at the center of the solution, we must make sure that their attention is focused on the most urgent things. Our systems already generate huge amounts of video data, alerts, log-ins and much more. We are beginning to see new information, in growing volumes, both from the IOT scene and related cyber segments. We are now putting intensive effort into UX and UI design, to make all human interactions much more manageable and with better results. In addition, we invest time and effort in ongoing training of operators who are the people on-site, thus combining advanced technologies with properly trained operators, to receive the type of security the client is aiming for.
THE IMPORTANCE OF UX & UI DESIGN
Keeping things simple for the user is a core value. This art is well established in the mobile world, where attention span is calculated in milliseconds. One might say that command & control systems enjoy a captive audience and exclusivity, but this is simply not true. Nobody should be taken for granted; if simplicity is not there, clients will abandon and refuse to come back.
GLOSEC SECURITY APPLICATION (GSA)
Connecting Security Systems and People

The Command Center (CC) sends automatic and personalized commands to the different security guards. CC Operator is alerted only when anomalies are present or when immediate human input required.


Security guards provide immediate updates and initiate their predefined responses, ensuring rapid and accurate response
In the past, we received ready-made risk analysis, a sort of “copy-paste” form that was provided to us by the client or hired advisor. Gradually, our hands-on experience indicated that critical information infrastructures involve risks that needed our close attention. Technological progress provides a wide range of options, and the choice between them is affected by intelligent and accurate analysis of the risk factors and the unique characteristics of a specific site.
In each project we develop unique knowledge. We perform risk analysis, and study each facility in detail based on international standards (ICAO, TSA ISPS, ISO27001 for Cybersecurity). These thorough surveys take into consideration threat analysis, vulnerabilities and gap analysis which lead to risk assessment. All this is achieved by mapping the near and distant surroundings, and interviewing all security staff from the guard through HR up to stakeholders. We document everything, leaving nothing to chance. This widespread and detailed effort is the foundation for an operational security plan. Today we know that this is a critical database which must be available to users of the system, and upon which we develop the methodology which will operate the security system, the SOP (Standard Operating Procedures).
Normally, manufacturers and integrators like ourselves would focus on selling the hardware. The software (i.e. the security management system) is intended to integrate all hardware and software components into one system. This is a process of applying engineering experience and knowhow in order to reduce costs and maintain performance. Buying equipment from a sole manufacturer can reduce the technological risk of combining products from different manufactures, however, it also “averages” the total performance of the system. In today’s global market there are many niche manufacturers that have unique products with exceptional solutions. Such products might not have been integrated into a system where all components are from a single source. Being an integrator focusing on the end-user, Glosec scans the market looking precisely for these unique products that can “spice up” a solution and generate a competitive result, a special value proposition.
Based on our vast experience, Glosec’s engineering team now approach each project “Bottom Up” (from the peripheral equipment, sensor, etc.), to the Command & Control, and also “Top Down”. This will enable us to maintain excellent performance across the system, and to verify that all components work as a one unified system and generate a Best of Breed Solution.
Protocols and procedures translate the desired behavior of the organization’s personnel into formal and practical guidelines for day-to-day management.
Security protocols should be built upon structured hierarchy to enable flexibility in the case of an event where constant evolution and communication are mission critical. The organizational security policy should consist of high-level directions, and specific policies provide more detailed guidance on how to put these principles into practice; they influence the way decision making aligns with the principles.
Ongoing training and courses are the cornerstone of every human resource participating in security. In order to carry out their respective tasks, all personnel must practice and drill so when an actual security event occurs they can automatically react to the challenge and perform as expected.
We have developed particular syllabuses for each function in the security arena. These courses begin from the guard and climb up to directors and stakeholders who lead the security policy in the organization
Last but not least, the most obvious yet sometimes the most overlooked part of the entire equation is proper maintenance. Security & safety systems are only as good as their continued maintenance. Glosec offers Corrective Maintenance based on agreed SLA (Service Level Agreement) which could be 24/7 for sensitive sites or NBD (Next Business Day) for less critical systems, as well as Preventive Maintenance to verify that all system elements are working properly.
Maintenance is extremely relevant in areas where installers might not stay around to support and maintain the system. Glosec sells and guarantees first class systems, as well as a promise to be here for long time, to continue to support our products, upgrades and future installations.

